Azure Subnet Peering
Currently, the subnet peering feature is available in all Azure regions, but it can only be configured using Terraform, PowerShell, API, Azure CLI, and ARM templates.
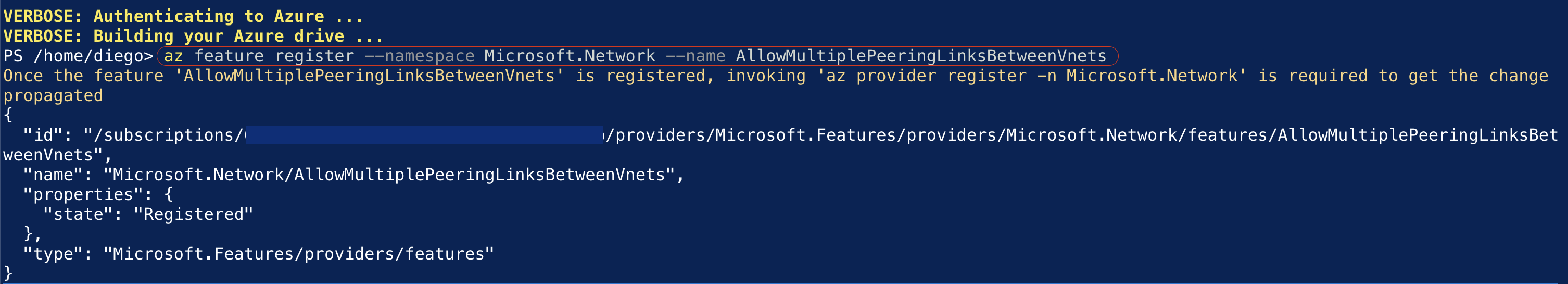
To use this feature, you must register the AllowMultiplePeeringLinksBetweenVnets feature in the Microsoft.Network namespace.
If you haven’t done this yet, you can use the following CLI command to register the feature and update the provider:
1
2
az feature register --namespace Microsoft.Network --name AllowMultiplePeeringLinksBetweenVnets && \
az provider register -n Microsoft.Network
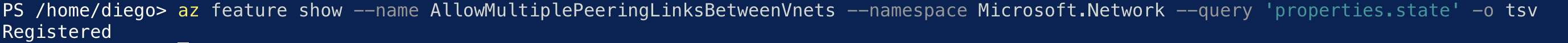
Then confirm that the feature was successfully registered using the following command:
1
az feature show --name AllowMultiplePeeringLinksBetweenVnets --namespace Microsoft.Network --query 'properties.state' -o tsv
After that, you can start testing the subnet peering feature between VNets.
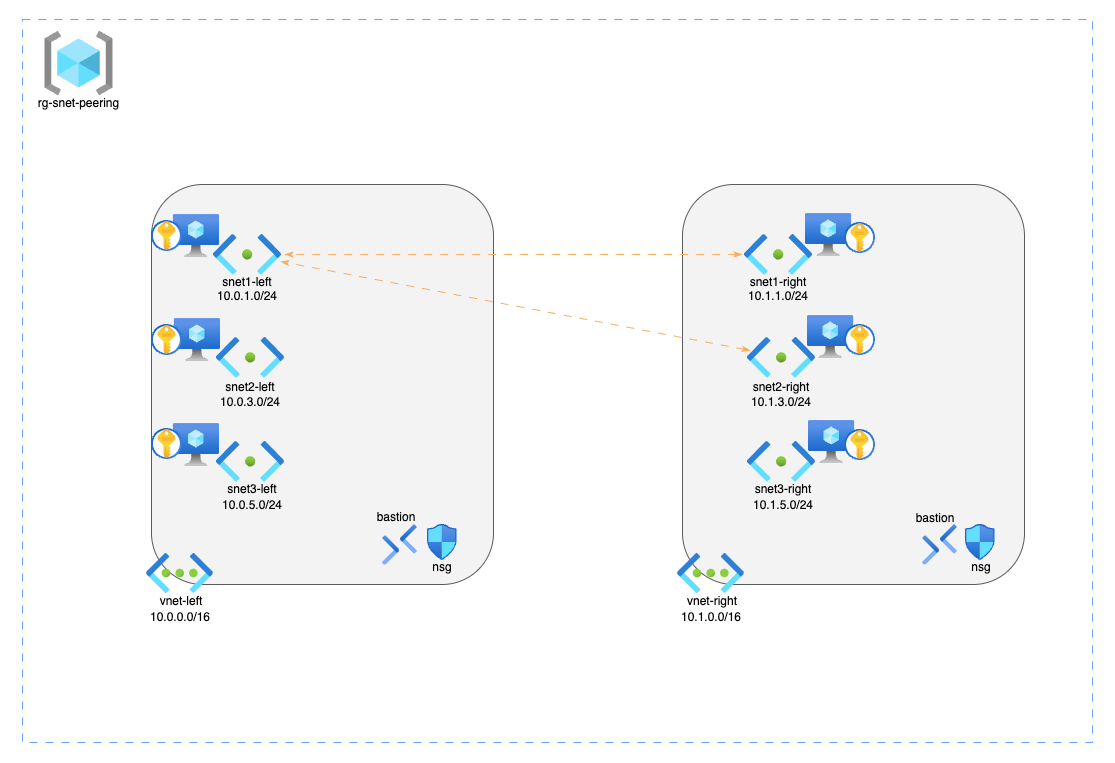
To test and explore this functionality, I created a sample lab architecture using Terraform, available on GitHub
- null_resource: executes a local-exec provisioner to register the feature
AllowMultiplePeeringLinksBetweenVnetsand update the provider. - Resource Group:
rg-snet-peering— contains all lab resources. - Network Security Groups (NSG):
nsg-left,nsg-right— control traffic for the subnets. - Virtual Networks (VNets) and Subnets:
vnet-left(10.0.0.0/16)snet1-left(10.0.1.0/24)snet2-left(10.0.3.0/24)snet3-left(10.0.5.0/24)
vnet-right(10.1.0.0/16)snet1-right(10.1.1.0/24)snet2-right(10.1.3.0/24)snet3-right(10.1.5.0/24)
NOTE: Peering is configured only betweensnet1-lefttosnet1-right,snet2-rightand vice-versa.
- Bastion Hosts:
bas-vnet-left,bas-vnet-right— secure access to VMs. - null_resource: executes a local-exec provisioner to register the feature
EncryptionAtHost. - Key Vault: stores the SSH private key for VM access.
- Virtual Machines (VMs): one VM per subnet for testing.
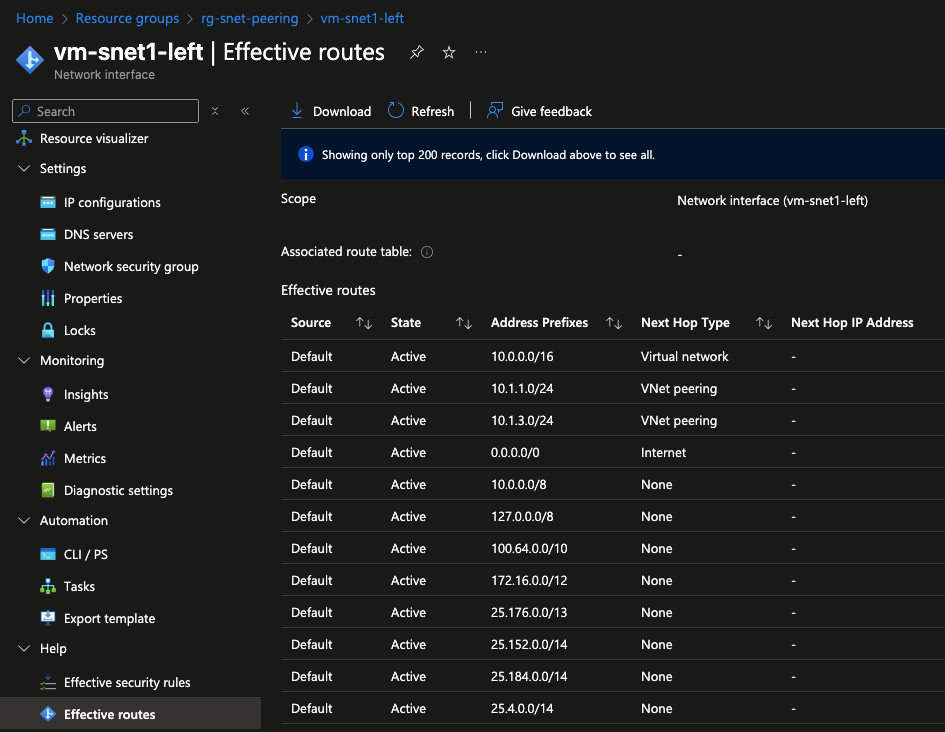
After deploying the resources, navigate to vnet-left under Settings > Address space. Here, you’ll notice that the address spaces for the remote subnets snet1-right and snet2-right are visible. You can also verify connectivity by checking the effective routes on each NIC. 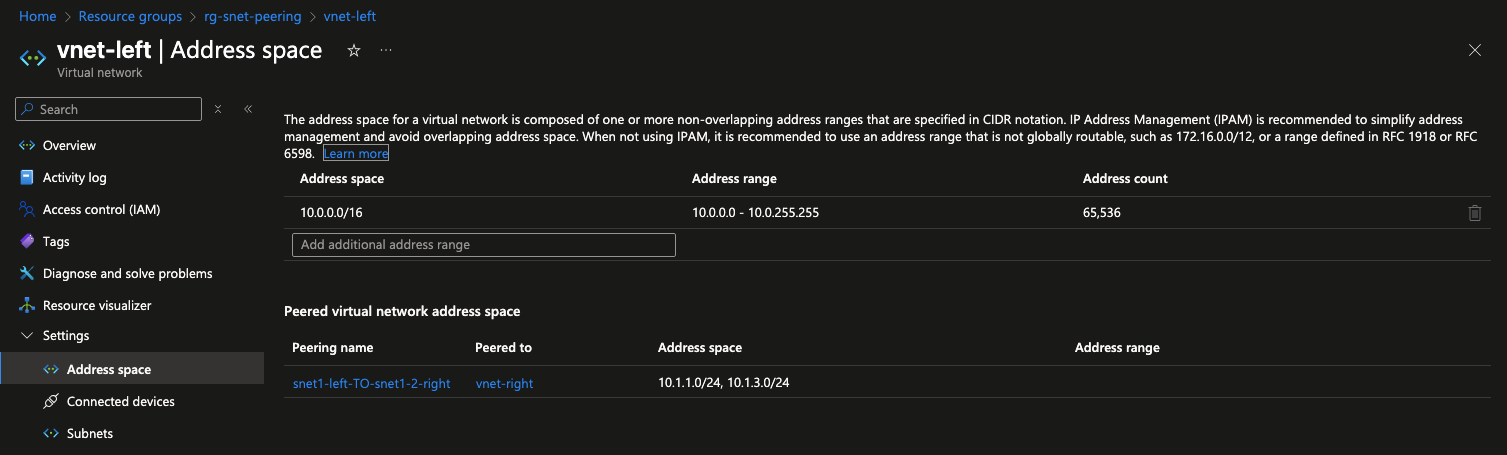
In vnet-right under Settings > Address space you will see the address space for the remote subnet snet1-left. 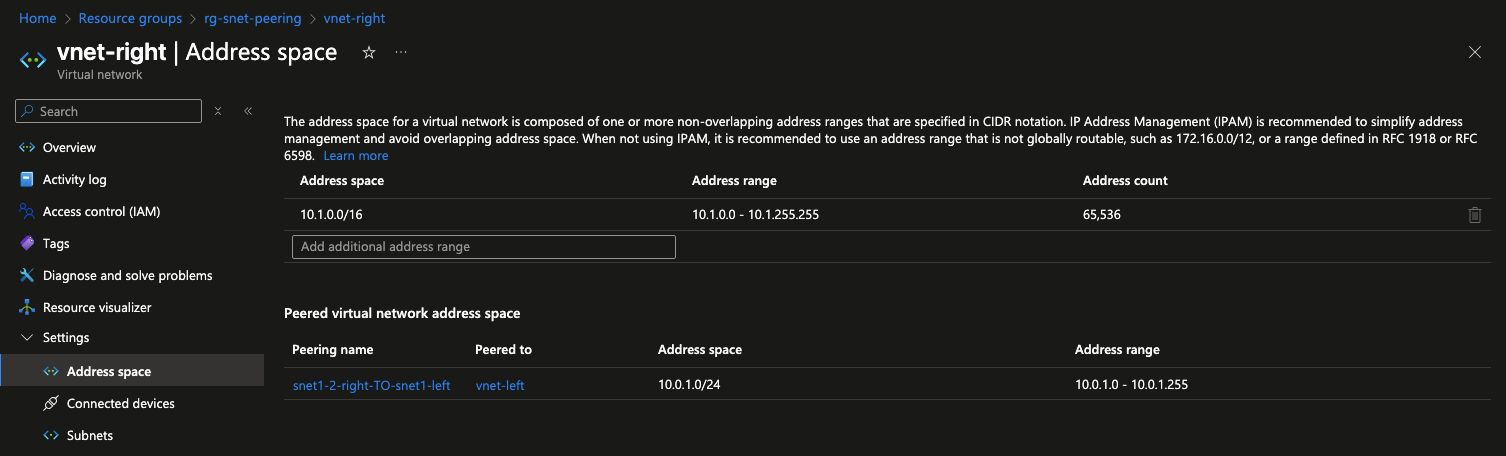
When you access vm-snet1-left via Bastion and try to ping vm-snet1-right and vm-snet2-right, the ping works as expected. However, if you try to ping vm-snet3-right, the ping fails because there is no peering configured between these subnets. 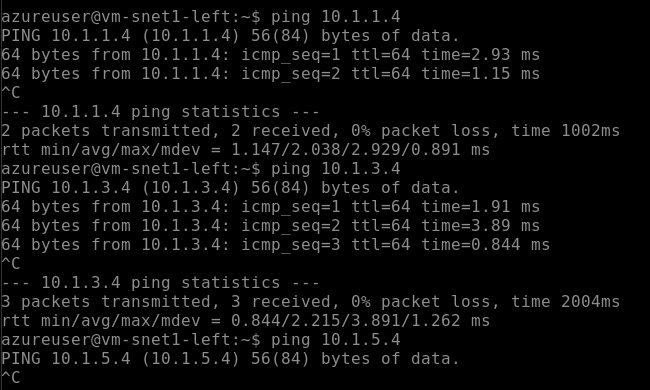
However, if you access vm-snet3-right and try to ping any subnet in vnet-left, it will not work because there is no peering configured between these subnets. 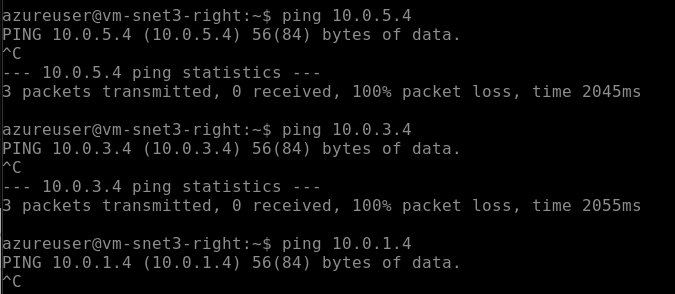
If you want to experiment with the lab by disabling peering between the subnets, simply set the enable_peering variable to false.
I’m also adding some reference links on the topic published by Microsoft
Subnet Peering
Introducing Subnet Peering in Azure
How to configure subnet peering
More details about Bastion Developer